|
File auditcsv { |
|
DestinationPath = 'C:\windows\temp\polaudit.csv' |
|
Ensure = 'Present'; |
|
Force = $true |
|
Contents = @' |
|
"Subcategory","Subcategory GUID","Inclusion Setting","Exclusion Setting" |
|
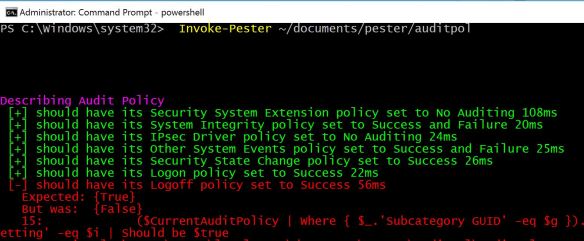
"Security System Extension","{0CCE9211-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"System Integrity","{0CCE9212-69AE-11D9-BED3-505054503030}","Success and Failure", |
|
"IPsec Driver","{0CCE9213-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Other System Events","{0CCE9214-69AE-11D9-BED3-505054503030}","Success and Failure", |
|
"Security State Change","{0CCE9210-69AE-11D9-BED3-505054503030}","Success", |
|
"Logon","{0CCE9215-69AE-11D9-BED3-505054503030}","Success and Failure", |
|
"Logoff","{0CCE9216-69AE-11D9-BED3-505054503030}","Success", |
|
"Account Lockout","{0CCE9217-69AE-11D9-BED3-505054503030}","Success", |
|
"IPsec Main Mode","{0CCE9218-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"IPsec Quick Mode","{0CCE9219-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"IPsec Extended Mode","{0CCE921A-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Special Logon","{0CCE921B-69AE-11D9-BED3-505054503030}","Success", |
|
"Other Logon/Logoff Events","{0CCE921C-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Network Policy Server","{0CCE9243-69AE-11D9-BED3-505054503030}","Success and Failure", |
|
"User / Device Claims","{0CCE9247-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"File System","{0CCE921D-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Registry","{0CCE921E-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Kernel Object","{0CCE921F-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"SAM","{0CCE9220-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Certification Services","{0CCE9221-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Application Generated","{0CCE9222-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Handle Manipulation","{0CCE9223-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"File Share","{0CCE9224-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Filtering Platform Packet Drop","{0CCE9225-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Filtering Platform Connection","{0CCE9226-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Other Object Access Events","{0CCE9227-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Detailed File Share","{0CCE9244-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Removable Storage","{0CCE9245-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Central Policy Staging","{0CCE9246-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Non Sensitive Privilege Use","{0CCE9229-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Other Privilege Use Events","{0CCE922A-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Sensitive Privilege Use","{0CCE9228-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Process Creation","{0CCE922B-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Process Termination","{0CCE922C-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"DPAPI Activity","{0CCE922D-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"RPC Events","{0CCE922E-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Authentication Policy Change","{0CCE9230-69AE-11D9-BED3-505054503030}","Success", |
|
"Authorization Policy Change","{0CCE9231-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"MPSSVC Rule-Level Policy Change","{0CCE9232-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Filtering Platform Policy Change","{0CCE9233-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Other Policy Change Events","{0CCE9234-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Audit Policy Change","{0CCE922F-69AE-11D9-BED3-505054503030}","Success", |
|
"User Account Management","{0CCE9235-69AE-11D9-BED3-505054503030}","Success", |
|
"Computer Account Management","{0CCE9236-69AE-11D9-BED3-505054503030}","Success", |
|
"Security Group Management","{0CCE9237-69AE-11D9-BED3-505054503030}","Success", |
|
"Distribution Group Management","{0CCE9238-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Application Group Management","{0CCE9239-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Other Account Management Events","{0CCE923A-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Directory Service Changes","{0CCE923C-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Directory Service Replication","{0CCE923D-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Detailed Directory Service Replication","{0CCE923E-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Directory Service Access","{0CCE923B-69AE-11D9-BED3-505054503030}","Success", |
|
"Kerberos Service Ticket Operations","{0CCE9240-69AE-11D9-BED3-505054503030}","Success", |
|
"Other Account Logon Events","{0CCE9241-69AE-11D9-BED3-505054503030}","No Auditing", |
|
"Kerberos Authentication Service","{0CCE9242-69AE-11D9-BED3-505054503030}","Success", |
|
"Credential Validation","{0CCE923F-69AE-11D9-BED3-505054503030}","Success", |
|
'@ |
|
} |
|
Script AuditPolicy { |
|
GetScript = { |
|
@{ |
|
GetScript = $GetScript |
|
SetScript = $SetScript |
|
TestScript = $TestScript |
|
Result = (& (gcm auditpol.exe) @('/get','/category:*','/r') | ConvertFrom-Csv | Select Subcategory*,*lusion*) |
|
} |
|
} |
|
SetScript = { |
|
Import-Csv -Path 'C:\windows\temp\polaudit.csv' | ForEach-Object { |
|
$g = $_.'Subcategory GUID' |
|
|
|
Switch ($_.'Inclusion Setting') { |
|
'No Auditing' { |
|
& (gcm auditpol.exe) @('/set',"/subcategory:$($g)",'/failure:disable','/success:disable') |
|
break |
|
} |
|
'Success' { |
|
& (gcm auditpol.exe) @('/set',"/subcategory:$($g)",'/failure:disable','/success:enable') |
|
break |
|
} |
|
'Failure' { |
|
& (gcm auditpol.exe) @('/set',"/subcategory:$($g)",'/failure:enable','/success:disable') |
|
break |
|
} |
|
'Success and Failure' { |
|
& (gcm auditpol.exe) @('/set',"/subcategory:$($g)",'/failure:enable','/success:enable') |
|
break |
|
} |
|
default {} |
|
} |
|
} |
|
} |
|
TestScript = { |
|
if( |
|
Compare-Object -ReferenceObject (Import-Csv 'C:\windows\temp\polaudit.csv') ` |
|
-DifferenceObject (& (gcm auditpol.exe) @('/get','/category:*','/r') | ConvertFrom-Csv | Select Subcategory*,*lusion*) |
|
) { |
|
return $false |
|
} else { |
|
return $true |
|
} |
|
} |
|
DependsOn = '[File]auditcsv' |
|
} |