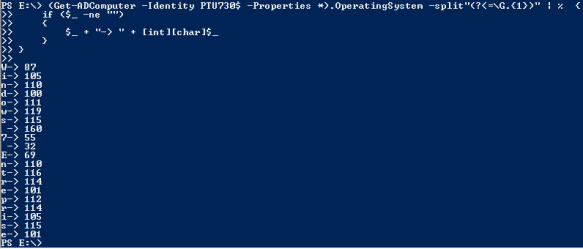
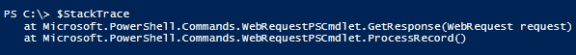
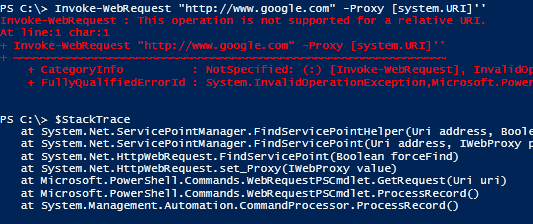
One of my favorite tip in powershell V2 is the following command that shows the code behind the tab completion feature:
(dir Function:\TabExpansion).Definition
Now, in powershell 3 beta on Windows 8, there’s a new cmdlet type called CIM. Once you have invoked a CIM cmdlet, you can explore its code.
Here’s how to see how many CIM cmdlets there are per module:
Get-Command -Capability CIM | Group-Object -Property ModuleName
Here’s how to explore the code of the new Get-NetIPAddress
(dir Function:\Get-NetIPAddress).Definition
and the code behind:
[CmdletBinding(DefaultParameterSetName='ByIPv4', PositionalBinding=$false)]
[OutputType([Microsoft.Management.Infrastructure.CimInstance])]
[OutputType('Microsoft.Management.Infrastructure.CimInstance#ROOT/StandardCimv2/MSFT_NetIPAddress')]
param(
[Parameter(ParameterSetName='ByIPv4')]
[ValidateNotNull()]
[string[]]
${IPv4Address},
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[string[]]
${IPv6Address},
[Parameter(ParameterSetName='ByIPv4', ValueFromPipeline=$true, ValueFromPipelineByPropertyName=$true)]
[Parameter(ParameterSetName='ByIPv6', ValueFromPipeline=$true, ValueFromPipelineByPropertyName=$true)]
[Alias('ifIndex')]
[ValidateNotNull()]
[System.UInt32[]]
${InterfaceIndex},
[Parameter(ParameterSetName='ByIPv4', ValueFromPipelineByPropertyName=$true)]
[Parameter(ParameterSetName='ByIPv6', ValueFromPipelineByPropertyName=$true)]
[Alias('ifAlias')]
[ValidateNotNull()]
[string[]]
${InterfaceAlias},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[Microsoft.PowerShell.Cmdletization.GeneratedTypes.NetIPAddress.AddressFamily[]]
${AddressFamily},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[Microsoft.PowerShell.Cmdletization.GeneratedTypes.NetIPAddress.Type[]]
${Type},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[byte[]]
${PrefixLength},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[Microsoft.PowerShell.Cmdletization.GeneratedTypes.NetIPAddress.PrefixOrigin[]]
${PrefixOrigin},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[Microsoft.PowerShell.Cmdletization.GeneratedTypes.NetIPAddress.SuffixOrigin[]]
${SuffixOrigin},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[Microsoft.PowerShell.Cmdletization.GeneratedTypes.NetIPAddress.AddressState[]]
${AddressState},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[System.TimeSpan[]]
${ValidLifetime},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[System.TimeSpan[]]
${PreferredLifetime},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[bool[]]
${SkipAsSource},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[ValidateNotNull()]
[Microsoft.PowerShell.Cmdletization.GeneratedTypes.NetIPAddress.Store[]]
${Store},
[Parameter(ParameterSetName='ByIPv4', ValueFromPipeline=$true)]
[Parameter(ParameterSetName='ByIPv6', ValueFromPipeline=$true)]
[PSTypeName('Microsoft.Management.Infrastructure.CimInstance#root/standardcimv2/MSFT_NetIPInterface')]
[ValidateNotNull()]
[Microsoft.Management.Infrastructure.CimInstance]
${AssociatedIPInterface},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[Alias('Session')]
[ValidateNotNullOrEmpty()]
[Microsoft.Management.Infrastructure.CimSession[]]
${CimSession},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[int]
${ThrottleLimit},
[Parameter(ParameterSetName='ByIPv4')]
[Parameter(ParameterSetName='ByIPv6')]
[switch]
${AsJob})
DynamicParam {
try
{
if (-not $__cmdletization_exceptionHasBeenThrown)
{
$__cmdletization_objectModelWrapper = Microsoft.PowerShell.Utility\New-Object $script:ObjectModelWrapper
$__cmdletization_objectModelWrapper.Initialize($PSCmdlet, $script:ClassName, $script:ClassVersion, $script:ModuleVersion, $script:PrivateData)
if ($__cmdletization_objectModelWrapper -is [System.Management.Automation.IDynamicParameters])
{
([System.Management.Automation.IDynamicParameters]$__cmdletization_objectModelWrapper).GetDynamicParameters()
}
}
}
catch
{
$__cmdletization_exceptionHasBeenThrown = $true
throw
}
}
Begin {
$__cmdletization_exceptionHasBeenThrown = $false
try
{
__cmdletization_BindCommonParameters $__cmdletization_objectModelWrapper $PSBoundParameters
$__cmdletization_objectModelWrapper.BeginProcessing()
}
catch
{
$__cmdletization_exceptionHasBeenThrown = $true
throw
}
}
Process {
try
{
if (-not $__cmdletization_exceptionHasBeenThrown)
{
$__cmdletization_queryBuilder = $__cmdletization_objectModelWrapper.GetQueryBuilder()
if ($PSBoundParameters.ContainsKey('IPv4Address') -and (@('ByIPv4') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${IPv4Address})
$__cmdletization_queryBuilder.FilterByProperty('IPv4Address', $__cmdletization_values, $true, 'Default')
}
if ($PSBoundParameters.ContainsKey('IPv6Address') -and (@('ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${IPv6Address})
$__cmdletization_queryBuilder.FilterByProperty('IPv6Address', $__cmdletization_values, $true, 'Default')
}
if ($PSBoundParameters.ContainsKey('InterfaceIndex') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${InterfaceIndex})
$__cmdletization_queryBuilder.FilterByProperty('InterfaceIndex', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('InterfaceAlias') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${InterfaceAlias})
$__cmdletization_queryBuilder.FilterByProperty('InterfaceAlias', $__cmdletization_values, $true, 'Default')
}
if ($PSBoundParameters.ContainsKey('AddressFamily') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${AddressFamily})
$__cmdletization_queryBuilder.FilterByProperty('AddressFamily', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('Type') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${Type})
$__cmdletization_queryBuilder.FilterByProperty('Type', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('PrefixLength') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${PrefixLength})
$__cmdletization_queryBuilder.FilterByProperty('PrefixLength', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('PrefixOrigin') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${PrefixOrigin})
$__cmdletization_queryBuilder.FilterByProperty('PrefixOrigin', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('SuffixOrigin') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${SuffixOrigin})
$__cmdletization_queryBuilder.FilterByProperty('SuffixOrigin', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('AddressState') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${AddressState})
$__cmdletization_queryBuilder.FilterByProperty('AddressState', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('ValidLifetime') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${ValidLifetime})
$__cmdletization_queryBuilder.FilterByProperty('ValidLifetime', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('PreferredLifetime') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${PreferredLifetime})
$__cmdletization_queryBuilder.FilterByProperty('PreferredLifetime', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('SkipAsSource') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${SkipAsSource})
$__cmdletization_queryBuilder.FilterByProperty('SkipAsSource', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('Store') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_values = @(${Store})
$__cmdletization_queryBuilder.FilterByProperty('Store', $__cmdletization_values, $false, 'Default')
}
if ($PSBoundParameters.ContainsKey('AssociatedIPInterface') -and (@('ByIPv4', 'ByIPv6') -contains $PSCmdlet.ParameterSetName )) {
$__cmdletization_queryBuilder.FilterByAssociatedInstance(${AssociatedIPInterface}, 'MSFT_NetIPInterfaceIPAddress', 'Antecedent', 'Dependent', 'Default')
}
$__cmdletization_objectModelWrapper.ProcessRecord($__cmdletization_queryBuilder)
}
}
catch
{
$__cmdletization_exceptionHasBeenThrown = $true
throw
}
}
End {
try
{
if (-not $__cmdletization_exceptionHasBeenThrown)
{
$__cmdletization_objectModelWrapper.EndProcessing()
}
}
catch
{
throw
}
}
# .EXTERNALHELP MSFT_NetIPAddress.cdxml-Help.xml