I’ve seen recently the following knowledge base article http://support.microsoft.com/kb/2761899 about Hyper-V VMM service fails and Event ID 14050 is logged when dynamicportrange is changed in Windows Server 2012
I was surprised that not everybody uses Powershell especially when running on Windows 2012 server.
I’ll show how to replace the following vbscript from KB2761899…
'This VBScript adds a port range from 9000 to 9999 for outgoing traffic
'run as cscript addportrange.vbs on the hyper-v host
option explicit
'IP protocols
const NET_FW_IP_PROTOCOL_TCP = 6
const NET_FW_IP_PROTOCOL_UDP = 17
'Action
const NET_FW_ACTION_BLOCK = 0
const NET_FW_ACTION_ALLOW = 1
'Direction
const NET_FW_RULE_DIR_IN = 1
const NET_FW_RULE_DIR_OUT = 2
'Create the FwPolicy2 object.
Dim fwPolicy2
Set fwPolicy2 = CreateObject("HNetCfg.FwPolicy2")
'Get the Service Restriction object for the local firewall policy.
Dim ServiceRestriction
Set ServiceRestriction = fwPolicy2.ServiceRestriction
'If the service requires sending/receiving certain type of traffic, then add "allow" WSH rules as follows
'Get the collection of Windows Service Hardening networking rules
Dim wshRules
Set wshRules = ServiceRestriction.Rules
'Add outbound WSH allow rules
Dim NewOutboundRule
Set NewOutboundRule = CreateObject("HNetCfg.FWRule")
NewOutboundRule.Name = "Allow outbound traffic from service to TCP 9000 to 9999"
NewOutboundRule.ApplicationName = "%systemDrive%\WINDOWS\system32\vmms.exe"
NewOutboundRule.ServiceName = "vmms"
NewOutboundRule.Protocol = NET_FW_IP_PROTOCOL_TCP
NewOutboundRule.RemotePorts = "9000-9999"
NewOutboundRule.Action = NET_FW_ACTION_ALLOW
NewOutboundRule.Direction = NET_FW_RULE_DIR_OUT
NewOutboundRule.Enabled = true
wshRules.Add NewOutboundRule
'end of script
…with a 3 lines Powershell script using the exact same approach.
$rule = New-Object -ComObject HNetCfg.FWRule -Property @{
Name = "Allow outbound traffic from service to TCP 9000 to 9999"
Direction = 2
Enabled = $true
ApplicationName = "$($env:systemdrive)\WINDOWS\system32\vmms.exe"
ServiceName = "vmms"
Protocol = 6
}
$rule.RemotePorts = "9000-9999"
(New-Object -ComObject HNetCfg.FwPolicy2).ServiceRestriction.Rules.Add($rule)
It isn’t actually done in 2 lines because of the intricacies related to the INetFwRule interface comobject
Now that I created the rule how do I list these new firewall rules?
There are actually two ways.
Either using ComObject
(New-Object -ComObject HNetCfg.FwPolicy2).ServiceRestriction.Rules
…or using the built-in Powershell commands of the NetSecurity module as we run on a Windows Server 2012 😀
Get-NetFirewallRule -PolicyStore ConfigurableServiceStore
If there’s a way to query these rules, there must be a way to create these rules.
And…here’s the one-liner (split in two lines using splatting for a better readability)
$HT = @{
DisplayName = "Allow outbound traffic from service to TCP 9000 to 9999"
Direction = "Outbound"
InterfaceType = "Any"
Action = "Allow"
Protocol = "TCP"
Service = "vmms"
Program = "$($env:systemdrive)\WINDOWS\system32\vmms.exe"
Enabled = "TRUE"
RemotePort = "9000-9999"
PolicyStore = "ConfigurableServiceStore"
}
New-NetFirewallRule @HT
Note that you can see the rule added in the registry as well under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SharedAccess\Parameters\FirewallPolicy\RestrictedServices\Configurable\System key (Source: http://blogs.technet.com/b/voy/archive/2007/04/02/network-restrictions-for-service-hardening.aspx )
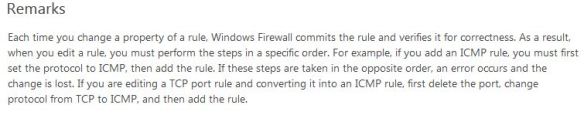
Let’s have a look at the PolicyStore parameter.
Get-Help Get-NetFirewallRule -ParameterName PolicyStore
While the help states that …
— ActiveStore: This store contains the currently active policy, which is the sum of all policy stores that apply to the computer. This is the resultant set of policy (RSOP) for the local computer (the sum of all GPOs that apply to the computer), and the local stores (the PersistentStore, the static Windows service hardening (WSH), and the configurable WSH).
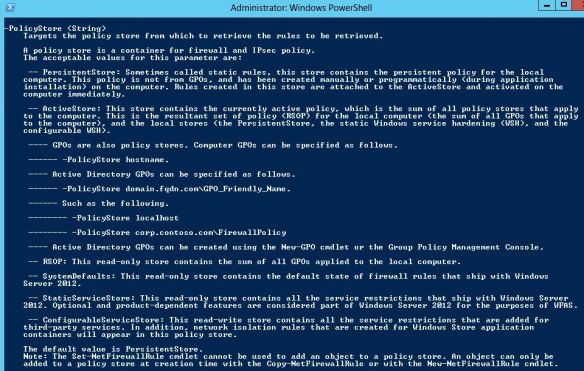
…my experience shows that the static and configurable WSH are not part of the ActiveStore.
Maybe that’s why these 2 stores are at same level as the Persistent and ActiveStore.
# "VMMSAllowRDPIn" isn't in ActiveStore Get-NetFirewallRule -Name "VMMSAllowRDPIn" -PolicyStore ActiveStore # but it's in the ConfigurableServiceStore Get-NetFirewallRule -Name "VMMSAllowRDPIn" -PolicyStore configurableServiceStore # And you cannot get it like like this... Get-CimInstance -Namespace root/StandardCimv2 -ClassName MSFT_NetFirewallRule | ? InstanceID -match "VMMSAllowRDPIn"
and I still wonder how I can get it? 😦
Another nice post 🙂 Bon boulot
Merci 😀
Pingback: Hyper-V-VMMS Event ID 14050 — Failed to register the service principal name ‘Hyper-V Replica Service’. Возвращаясь в к проблеме регистрации SPN в Windows Server 2012 R2 | Блог IT-KB
Awesome explanation, thanks.
Nice Post but it does not solve the Hyper-V-VMMS Event ID 14050 crisis.
SNMP Extension Agent on Windows Server 2012 unable to connect to a port from which it needs data
http://stackoverflow.com/questions/25419192/snmp-extension-agent-on-windows-server-2012-unable-to-connect-to-a-port-from-whi
Pingback: Griffon's IT Library » Hyper-V » Tip : Hyper-V Failed to register service principal name – ID 14050
Pingback: Hyper-V replika gondok | Asteriksz's Blog
Yes i just found these WHS rules whilst looking at the registry and i think they should be called MBR for Microsoft Backdoor Rules instead.
Windows 10 is calling home like never before and us developers are being locked out all over the place when we try to make computers safe and have to hack the registry all the time so long as the next update does not lock us out even more on registry keys that you can own but still are not allowed to edit values.
Shocking that MS is allowed to get away with this
Pingback: Hyper-V-VMMS Event ID 14050 - Failed to register the service principal name 'Hyper-V Replica Service'. Возвращаясь в к проблеме регистрации SPN в Windows Server 2012 R2 - Блог IT-KB